This article was originally published by Lili on Medium
This piece walks a user through how to discreetly travel with bitcoin, or any piece of information they wish to keep private, using steganography. This technique eliminates the human error involved with using a brain wallet (simply memorizing your seed phrase).

What is Steganography?
Steganography, as it applies to computing, is the process of concealing a sensitive file or message within another ordinary file (be it a plaintext file, image, video, or sound file).
A bitcoin holder’s use case for Steganography
This piece examines how one can use Steganography techniques to obfuscate sensitive information such as a bitcoin seed phrase or private key using nothing more than standard Linux tools. The technique discussed involves hiding a bitcoin seed phrase within a photograph in a user’s camera roll (a plain picture from a vacation).
Memorizing a seed phrase, writing the seed phrase on paper, and/or carrying a hardware wallet are not necessary in this case. This is ideal for an OPSEC conscious bitcoin holder or anyone operating in an adversarial environment.
NOTICE! The subject of steganography is extensive. This guide isn’t meant to be an exhaustive piece on this subject. A competent security researcher or dedicated adversary could in theory find the hidden files or break this model. This tutorial is simply an introduction to this subject and guide to implementing a steganography technique using common command-line tools. This guide serves as a starting point for advanced users who wish to research this subject in greater detail and develop a system of their own. Also, this piece is for information purposes only, this is not legal or financial advice.
Required Tools
To follow this tutorial, you will need a bash shell or terminal emulator.
If you are not using a Linux computer the following are available:
- Windows users: install Bash for Windows
- Mobile users: download Termux for Android on F-Droid (do not use the Google play version of Termux, it is broken and not updated!)
How to use Steganography to hide your seed phrase
STEP 1: Start by making a directory to store the files you wish to hide, enter the following command:

mkdir -p stego && cd stego/
STEP 2: Open a new file using your favorite text editor. In this example we’ll name the file `seed.txt`. Enter your 12–24 seed phrase words into this file, save, and close the editor. You can also use the “echo” command to place the words in the file like so:

echo "your passphrase" >seed.txt
STEP 3: Next we’re going to encrypt the text file we just made using openssl to provide an additional layer of security in case the secret file is discovered (enter the command below). Alternatively a user can use PGP if they are familiar with that.

openssl enc -aes-256-cbc -salt -a -in seed.txt -out seed.txt.enc
Upon entering this command you will be prompted to enter a password and verify it. Once that’s done and you are returned to your prompt, you can now delete the plaintext version of the file using this command:
rm seed.txt
STEP 4: Make another directory to store your file in for compression and save this file as a .zip file in order to make it accessible from most modern computers. In this example we’ll call the new directory “secrets”. Enter the following commands:

mkdir -p secrets mv seed.txt.enc secrets/ zip -r secrets.zip secrets/
Now we can delete the directory using the following command:

rm -rf secrets/
NOTE: The secrets directory was created simply to compress the file in zip form. The secrets.zip file is “outside” of the secrets/ directory. When you compress files using zip or tar in unix, the original folder remains intact. Therefore, you need to delete the secrets directory (as shown in the step above) because it contains the information you are hiding. You don’t want to leave copy of it on your computer for an adversary to find.
STEP 5: Using your file browser or preferred method, choose an image to use to store the secret zip file in, here we’ll call it `image.jpg`. Once you have both your image and zip file there, combine the two using the commands below. Since we are using a jpg image, we can rename the output file to “dubai.jpg” since it uses that same extension:

cat image.jpg secrets.zip > dubai.jpg
We now have an image containing our encrypted secrets file (the seed phrase) called “dubai.jpg” and can safely delete all the other files:

rm secrets.zip image.jpg
Anyone snooping using a file explorer would only see the picture (dubai.jpg) with no clue that a secret is hidden inside of it:
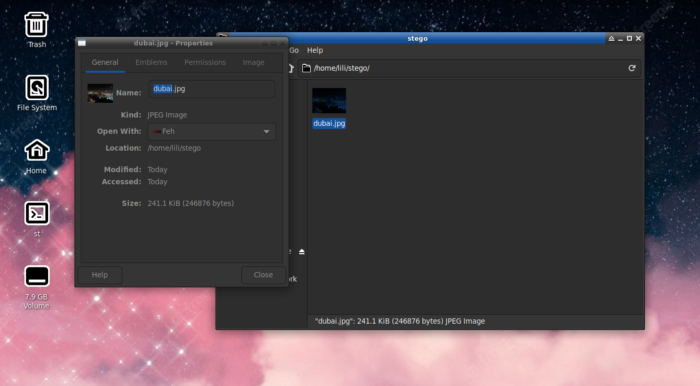
NOTE: A picture of the Dubai skyline taken while on vacation was chosen to hide the seed phrase in because an image like this is unlikely to raise eyebrows. Always chose a plain image, don’t be extravagant, and do not use images related to bitcoin.

STEP 6: Access the data hidden in the image, in this case, the seed phrase. To access this data, simply run:

unzip dubai.jpg
The folder containing the secret info you put in it by following the previous steps will now be accessible. If you encrypted the data using the OpenSSL step above, use the following command to decrypt it and enter your password when prompted. The file will be available in plaintext after this step.

openssl enc -aes-256-cbc -d -a -in seed.txt.enc -out seed.txt
STEP 7: Copy the seed phrase down on a piece of paper and then delete the plaintext file containing this information to preserve your secrecy.
STEP 8: Download a bitcoin wallet (ideally through F-Droid or direct APK download) and load the seed phrase into it. Now you can proceed to spend and receive bitcoin normally.
And that’s it! This method requires nothing besides a few standard unix tools and some patience. As for use cases outside of bitcoin seed phrases and private keys … your imagination is the limit!
Final thoughts
To recap, Steganography is a form of cryptography that allows anyone to conceal a sensitive piece of information within an ordinary file (be it a plaintext file, image, video, or sound file).
This technique is best for those who are extremely OPSEC conscious or operating in an adversarial environment. Regardless, this technique has many use cases and is a good skill to master.
If you liked this piece, please follow me for more! Questions? Send me a DM on Twitter @marketsbylili or an email to [email protected]



